Difference between revisions of "Ethernet capture"
| Line 1: | Line 1: | ||
The ethernet capture task and module can capture ethernet traffic from interfaces on the WCU in a format known as [[wikipedia:Pcap|pcap]]. This is a standarized format of saving packet information and can be used in many tools to be analyzed. As there can be a lot of traffic on ethernet interfaces, there is an option to enter a filtering expression (Capture expression) to only capture certain packets of interest. Examples and descriptions of filter expressions can be found [https://biot.com/capstats/bpf.html here] and [https://www.comparitech.com/net-admin/pcap-guide/ here]. | The ethernet capture task and module can capture ethernet traffic from interfaces on the WCU in a format known as [[wikipedia:Pcap|pcap]]. This is a standarized format of saving packet information and can be used in many tools to be analyzed. As there can be a lot of traffic on ethernet interfaces, there is an option to enter a filtering expression (Capture expression) to only capture certain packets of interest. Examples and descriptions of filter expressions can be found [https://biot.com/capstats/bpf.html here] and [https://www.comparitech.com/net-admin/pcap-guide/ here]. | ||
[[File:Screenshot from 2021-04-01 08-53-12.png|thumb|Creating an Ethernet capture task|350x350px]] | |||
== Ethernet interface and capture expression == | == Ethernet interface and capture expression == | ||
Revision as of 14:42, 31 August 2022
The ethernet capture task and module can capture ethernet traffic from interfaces on the WCU in a format known as pcap. This is a standarized format of saving packet information and can be used in many tools to be analyzed. As there can be a lot of traffic on ethernet interfaces, there is an option to enter a filtering expression (Capture expression) to only capture certain packets of interest. Examples and descriptions of filter expressions can be found here and here.
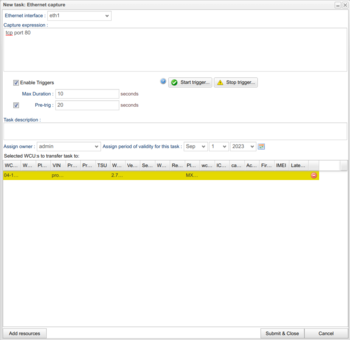
Ethernet interface and capture expression
To create a task of this type you need to at least enter the interface which you would like to capture from using the "Ethernet interface" drop-down selector at the top. Only interfaces available for the current platform will show. In the section "Capture expression" you simply enter the expression for capturing packets. Depending on the installation at your site, there might be a button for validating the expression "Validate expression". Press this to validate the expression. If this is not available, you could use any local tool available to you to validate the capture expression. Examples of such tools are tcpdump and wireshark.
When done, simply press "Submit & Close" to get the task down to the WCU.
Triggers
Start- and stop-triggers (Since 2.66)
It is possible to add trigger expressions that will start and/or stop the task. To do this, check the box "Enable Triggers". Use the buttons "Start trigger..." and "Stop trigger..." to add a start and stop trigger expression. Note that the signals that are used in the start and stop trigger expressions must be measured by the signal reader assignment on the WCU/s in question. It is possible to leave the Stop Trigger blank, but a Start Trigger must be supplied. It is also possible to set how long the capture should undergo after the Start trigger expression has been met by using the Max Duration field.
Pre-trigger duration (Since 2.67)
For WCUs with version 2.67 or later it is also possible to add a pre-trigger duration. By adding this, the traffic before the start trigger will be captured. How much before is given by the pre-trigger duration. I.e. if the pre-trigger is set to 20 seconds, the traffic happening from 20 seconds before the start trigger up until the start-trigger will also be captured and saved.
Analyzing Results
Th results from the captured data on the WCU is delivered as pcap files. This is a standardized binary format for captured ethernet packets. One of the most widely used tools to analyze such data is wireshark which is available for most computer platforms.